
How to Securely Manage Remote Work with Apps
Build with Retainr
Sell your products and services, manage clients, orders, payments, automate your client onboarding and management with your own branded web application.
Get Started1. What are the best apps for securely managing remote work?
Best Apps for Securely Managing Remote Work
Managing remote work can be challenging, especially when it comes to security. However, there are several apps available that are designed to make this task easier. Some of the best and most secure apps for managing remote work include:
- LastPass: A password manager that stores and encrypts your passwords. This eliminates the risk of forgetting passwords and decreases the likelihood of security breaches.
- Microsoft Teams: A collaboration tool that offers end-to-end encryption for video meetings and file sharing.
- VPN: Virtual Private Network apps, such as NordVPN or ExpressVPN, help secure internet connection and protect data.
- Slack: A communication platform with two-factor authentication to ensure secure communication within teams.
- MFA: Multi-Factor Authentication apps like Google Authenticator offer an extra layer of security by requiring at least two verification methods.
Parameters to Consider while Choosing Apps
While choosing the best app to manage remote work securely, several key factors need to be taken into account. The main criteria include data encryption, user authentication, features, ease of use, and user reviews. A comprehensive comparison of these parameters for some of the apps mentioned above is displayed in the following table:
| Application | Data Encryption | User Authentication | Features | Ease of Use | User Reviews |
|---|---|---|---|---|---|
| LastPass | Yes | Password | Stores passwords, auto-fill, password generator | High | 4.5/5 |
| Microsoft Teams | Yes | Password | Video meetings, screen sharing, file sharing | Medium | 4.0/5 |
Conclusion
Safety and efficiency are vital in managing remote work. While different apps serve various purposes, choosing an app that best suits your organization is fundamental. Ensuring encrypted connections, secured credentials along with user-friendly interfaces will enable a more secure and productive work-from-home environment.
2. How can apps ensure the security of remote work?
Implementing Security Features in Apps
Apps can ensure the security of remote work in several ways. First on the list is implementing advanced encryption technology. This technology makes data unreadable unless one has the key to decipher it. Secondly, apps can provide multi-factor authentication, which requires the user to verify their identity using more than one method. These could include something they know (password), something they own (mobile device), or something inherent (fingerprints or facial recognition). Lastly, apps can have auto-lock features, which lock the app after a certain period of inactivity, therefore preventing unauthorized access.
| Security Feature | Description |
|---|---|
| Advanced Encryption | Makes data unreadable without a deciphering key |
| Multi-Factor Authentication | Requires more than one method of identity verification |
| Auto-Lock | Locks the app after periods of inactivity to prevent unauthorized access |
Using Apps with Built-in Security Measures
Another way of ensuring security is using apps that have built-in security measures. These apps are developed with security as a central focus. They include end-to-end encrypted messaging apps, secure email providers, and cloud storage services with multiple levels of security. It’s essential to choose apps that continuously update their security features and promptly patch potential vulnerabilities. The use of intrusion detection systems (IDS) and intrusion prevention systems (IPS) in these apps can also provide additional layers of protection by monitoring network traffic for malicious activities.
Employee Training and Awareness
Even with the most secure apps, it is equally important to incorporate employee education and awareness programs regularly. Employees should be trained on good cybersecurity practices such as strong password protocols, recognizing phishing attempts, and secure use of Wi-Fi networks. They should also know the importance of promptly updating apps or operating systems when updates are available, as they often include essential security patches. In addition, employees need to understand how to use security features in the apps they use, including how to activate them, what they protect against, and reporting protocols for any security incidents.
3. Which features should I look for when selecting a secured app for remote work?
Essential Features of a Secure App for Remote Work
When selecting a secure app for remote work, there are several features you should consider. First, the app should have a robust security protocol, including strong encryption and two-way authentication features, which help to protect data being transmitted over the network. The app should also have a clear privacy policy stating how users’ data is collected, used, and protected.
- Encryption: This helps to protect your data as it moves across the network. Strong encryption such as 256-bit AES is ideal.
- Two-factor or multi-factor authentication: This offers an additional level of security by requiring you to verify your identity in two or more ways.
- Clear privacy policy: Knowing how your data is used and protected is crucial, so look for an app with a comprehensive and understandable privacy policy.
Other Important Features
Other noteworthy features to consider include user-friendly design, regular updates for security patches, and substantial customer support. It might also be helpful if the app is compatible with multiple devices and operating systems, and has offline capabilities for times where internet connectivity is poor.
| Feature | Explanation |
|---|---|
| User-friendly design | An intuitive interface can increase productivity. |
| Regular updates | Apps that are regularly updated are more likely to be secure against the latest threats. |
| Customer Support | Good customer support can assist with any issues or queries you may have. |
| Compatibility | Apps that work across different devices and operating systems offer greater flexibility in remote working conditions. |
| Offline capabilities | If the internet becomes inaccessible, offline features ensure work continuity. |
4. How can I safeguard sensitive data while using apps for remote work?
Safeguarding Sensitive Data: Principles & Practices
Ensuring the safety of sensitive data while using apps for remote work is critical in today's digitized and decentralized working environment. Adhering to secure data management principles and practices is paramount to avoid data breaches. Here are three fundamental principles to follow:
- Least Privilege: Ensure that users and applications have the least amount of data access necessary to perform their tasks.
- Encryption: Employ high-level encryption for sensitive data both at rest and in transit.
- Regular updates: Regularly update apps to receive the latest security patches and improvements.
Implementing Security Measures with Remote Work Apps
Apart from following these principles, there are specific steps you can utilize to enhance your security while using remote work apps:
| Step | Action |
|---|---|
| 1 | Opt for multi-factor authentication(F2A). This adds an extra layer of security by combining something the user knows (like a password) with something they have (like a verification code sent to their phone). |
| 2 | Use a virtual private network (VPN) when accessing and sharing sensitive data. This ensures a safe connection and protects data integrity. |
| 3 | Ensure that sensitive data is anonymized or pseudonymized where possible. This limits the potential damage in the event of a data breach. |
Vendor Management for App Security
Finally, managing the vendors or developers of the remote work apps you use is another aspect of data security. Ensure that the vendors are compliant with data privacy laws and have strong security practices. Here are three recommendations to do it:
- Audit the vendors for conformance with data security standards like ISO 27001 or SOC 2.
- Include data protection clauses in the service level agreements (SLAs) to hold vendors accountable for data breaches.
- Review the vendor’s data breach response plan to ensure they can effectively respond to and manage potential breaches.
5. What steps should I take to manage security risks while using apps for remote work?
Assessing and Prioritizing App Security
Firstly, remote work apps should be thoroughly reviewed and vetted before use. This includes researching the developer's reputation, checking for any reported security issues and confirming that the app has appropriate encryption measures in place. Apps that store sensitive data should also provide options for two-factor authentication. Some necessary steps to ensure application security are:
- Ensuring the use of secure, encrypted connections
- Regularly updating apps to the latest version
- Implementing two-factor authentication
- Checking the reputation of app developers
Securing Device and Network
Securing the device used for remote work is just as important as securing the applications. Strong passwords, biometric security and ensuring that devices are updated regularly helps in securing them. The use of a secure, private network is also essential as public Wi-Fi networks can expose data to security risks. Here are some steps to secure devices and networks:
- Setting strong, unique passwords on all devices
- Using biometric security features where available
- Regularly updating device's software
- Using a VPN for a secure network connection
Implementing a Security-Focused Company Culture
Inculcating a security-focused culture is a key step in managing security risks. Employees should be trained on safe cyber practices and the need to report any suspicious activity. A robust data backup plan should be in place in the event of a data breach. Establishing a company wide policy regarding security can help in maintaining and enhancing security measures. Essential aspects of a security-focused culture include:
| Aspect | Description |
|---|---|
| Cybersecurity training | Regular training sessions for employees on safe cyber practices. |
| Reporting mechanism | Establishing clear protocol for reporting suspicious activity or breaches. |
| Data backup plan | Regular backup of important data to a secure, preferably encrypted, location. |
| Security Policy | Developing a written security policy to be followed across the organization. |
6. Are there any specific security measures to consider while using video conferencing apps for remote work?
General Measures for Video Conferencing App Security
With the surge of remote work, the use of video conferencing apps has greatly increased, raising the alarm for their security. A few general measures that should be considered for securing your virtual meetings include:
- Choosing a video conferencing app with robust security settings and assuring those settings are suitably configured.
- Always using updated versions of the chosen app to take advantage of the latest security improvements.
- Initiating two-factor authentication when logging into the video conferencing app.
- Restricting what can be shared on the screen during meetings as well as who can share it.
- Refraining from sharing meeting links or IDs publicly.
App-Specific Security Measures
Different video conferencing apps come with specific security features and measures. For instance:
| App | Security Measures |
|---|---|
| Zoom | Offers waiting room and passcode features, and lets hosts manage participants, including removal, if necessary. |
| Microsoft Teams | Allows management of meeting options and participant behaviours, such as who can present and annotate. |
| Google Meet | Provides host control features, including deciding who to allow in and the ability to mute or remove participants. |
Participant Level Measures
While app settings and hosting practices are crucial, participants also have their part to play in securing video conferencing meetings. Important participant-level measures include:
- Being careful about clicking on links or files shared during the meeting.
- Likewise, being mindful of what they share on the platform, as it could potentially be seen by others.
- Being vigilant about phishing emails posing as video conferencing invitations or alerts.
7. How can I prevent unauthorized access when using apps for remote work?
Implementing Strong Authentication Measures
Preventing unauthorized access when using apps for remote work can be streamlined through strong authentication measures. This often includes Multi-Factor Authentication (MFA), which is an additional layer of security that ensures even if a password is compromised, the account remains secure. Apps like Google Authenticator or Authy can help in implementing MFA. Additionally, sticking to complex, unique passwords and utilizing a reliable password manager, like LastPass or 1Password, can reduce the risk of unauthorized access.
Creating a whitelist of approved devices that are allowed access to work systems, and enabling automatic system lockouts after a period of inactivity are additional measures to enhance security. It's also beneficial to access work-related apps through a Virtual Private Network (VPN) connection, which provides encryption and cloaks your IP address to guard against unauthorized data access.
Implementing Access Controls and Regular Software Updates
Access control is pivotal to preventing unauthorized access. It's advisable to implement Role-Based Access Control (RBAC) or Attribute-Based Access Control (ABAC) on business apps, which grant permissions based on the user's role or other user attributes. Some apps that support these functionalities include Okta and Azure Active Directory. Also, regular software updates are paramount to maintain app functionality and security. In most cases, software updates consist of patches and fixes to vulnerabilities that could be exploited by unauthorized individuals.
Secure Remote Work Access Matrix
| Security Measures | Relevant Apps |
|---|---|
| MFA | Google Authenticator, Authy |
| Password Managers | LastPass, 1Password |
| VPN | ExpressVPN, NordVPN |
| Access Control | Okta, Azure Active Directory |
8. How do I ensure that my employees are using secure apps for remote work?
Review and Approve Required Apps
Firstly, it is essential to outline which apps are necessary for your employees to execute their tasks. Additionally, you should understand the security protocols for these apps. Make a list of required tools and vet each for possible security risks. Check for features like two-factor authentication, data encryption, and regular security updates.
Consider the following actions:
- Engage IT or security experts in vetting these tools.
- Limit access to these tools only to necessary personnel.
- Train employees on secure use of these tools.
- Enforce a strong password policy for all tools.
- Review and update your chosen stack periodically.
Use of Personal Devices for Work Purposes
Personal devices often lack the rigorous security safeguards seen in office IT. Therefore, if company data is being accessed through them, security measures should be installed. Consider implementing a Bring Your Own Device (BYOD) policy that outlines required security standards. To illustrate, here are a few considerations:
| Action | Consideration |
|---|---|
| Implement Antivirus Software | Ensure that all personal devices have up-to-date antivirus software installed. |
| Enforce Firewall Usage | A firewall acts as the first line of defence against cyberattacks. |
| Secure Wi-Fi Connections | Discourage use of public Wi-Fi unless via a secure corporate VPN. |
| Automatic Lock and Password Protect | Dictate that devices must lock after a period of inactivity and require a secure password for entry. |
| Data Encryption | Encrypt sensitive data. This is especially crucial should a device get lost or stolen. |
Sustain Constant Engagement and Training
Finally, it's vital to ensure that employees are consistently adhering to the security guidelines outlined. A regular open dialogue prompts employees to share their concerns or challenges with remote tools. It also provides an opportunity to address any emerging security risks. Training should be ongoing, especially for newer hires, and should be revisited whenever major remote work tools are introduced or updated.
9. How important is end-to-end encryption in apps for remote work?
Understanding the Importance of End-to-End Encryption in Apps
End-to-end encryption is a vital feature in remote work apps. It ensures that the data transmitted between two endpoints- say, between you and your coworker, remains confidential and unintercepted by unauthorized third parties. Essentially, it translates the information into a code readable only by the parties involved. Let's take a dive into the key reasons explaining why end-to-end encryption is critically important for remote work:
- Confidentiality: The primary role of end-to-end encryption is maintaining confidentiality. Remote work often requires sharing sensitive information, and encryption ensures it’s seen only by the intended recipient. Any intercepted data is unintelligible to unauthorized parties.
- Data Protection: Encryption doesn’t just protect your discussions, it also acts as a security layer for shared files, protecting troves of company information from prying eyes.
- Maintaining Integrity: Besides confidentiality, end-to-end encryption protects from data tampering. That ensures that the transmitted data has not been altered during transport, preserving its original authenticity.
Choosing Apps with End-to-End Encryption
Considering the substantial role of end-to-end encryption, it becomes vital that remote work tools are chosen wisely. Here are a few notable apps that provide end-to-end encryption, creating a secure environment for remote team collaboration:
| App | Type |
|---|---|
| Zoom | Video Conferencing |
| Slack | Messaging |
| Google Drive | File Management |
| Tresorit | Cloud Storage |
For remote work to be efficient and secure, end-to-end encryption shouldn't be optional. As remote work continues to surge, investing in apps with this critical feature will be a wise move for businesses looking to protect their data and ensure team collaboration is secure and private.
10. Can apps for remote work protect my business from cybersecurity threats? How?
App Protection Against Cybersecurity Threats
Yes, remote work apps can significantly protect your business from cybersecurity threats. This is achieved through multiple measures, including end-to-end encryption- keeping your data secure during sending and receiving, two-factor authentication – providing an additional verification layer, and automatic software updates – to fix vulnerabilities and keep the protection updated. Additionally, user activity auditing is beneficial in monitoring any suspicious activity.
Details of Cybersecurity Measures
- End-to-end encryption: This ensures that the data transferred between users cannot be read by anyone else, even if intercepted. Essentially, it turns your data into a code during transmission, which can only be decoded with a unique key at the receiving endpoint.
- Two-Factor Authentication (2FA): This adds an extra layer of security to app access by requiring two types of identification - usually, something the user knows like a password, and something they have, like a verification code sent to their phone or fingerprints. This makes it much harder for unauthorized personnel to gain access to your data.
- Automatic Software Updates: Regular updates from your app provider not only provide new features, they also fix security glitches, preventing attacks from hackers who exploit software weaknesses.
- User Activity Auditing: This feature records all user activities, enabling admins to identify any suspicious actions taken within the app, hence it serves as a proactive measure against any potential threats.
Cybersecurity Measures Table
| Cybersecurity Measure | Description |
|---|---|
| End-to-End Encryption | Turning data into code during transmission, which can only be decoded with a unique key at the receiving end. |
| Two-Factor Authentication | Requiring two types of identification such as a password and a verification code sent to the user's phone, to provide additional security. |
| Automatic Software Updates | Periodically downloading and installing updates to fix any existing software vulnerabilities and introduce new features. |
| User Activity Auditing | Recording all user activities to identify any suspicious actions within the app. |
Conclusion
How to Securely Manage Remote Work with Apps
As businesses transition to a remote working setup, it is crucial to implement secure and efficient solutions to manage this new way of working. Remote work management apps such as Retainr.io can play a pivotal role in maintaining productivity, managing tasks, tracking work, and ensuring data security.
Secure Data Transmission with Retainr.io
Retainr.io offers a secure and highly functional platform for streamlining remote work. This whitelabel software ensures encrypted data transmission, allowing businesses to securely sell, manage clients, orders, and payments all within the confines of their own branded app. With Retainr.io, businesses can mitigate the risks of data breaches and cyberattacks.
Efficient Task Management
Beyond its robust security features, Retainr.io also scores high for efficiency. The software makes it easy to delegate tasks, track progress, and manage clients, all while minimizing potential disruptions associated with remote work. Retainr.io brings efficiency and organization to remote work, making the transition seamless and stress-free.
Selling Made Easy
One of the key advantages of Retainr.io is its functionality related to sales. It's a secure platform to sell, manage clientele, and oversee orders and payments. With Retainr.io, businesses can experience a marked improvement in their sales process, leading to enhanced revenues and business growth.
To learn more about how Retainr.io can streamline your remote work management needs, visit www.retainr.io.
Boost Your Agency Growth
with Retainr Accelerator
Uncover secrets, strategies, and exclusive blueprints to take your agency's growth to the next level — from marketing insights to effective presentations and leveraging technology.
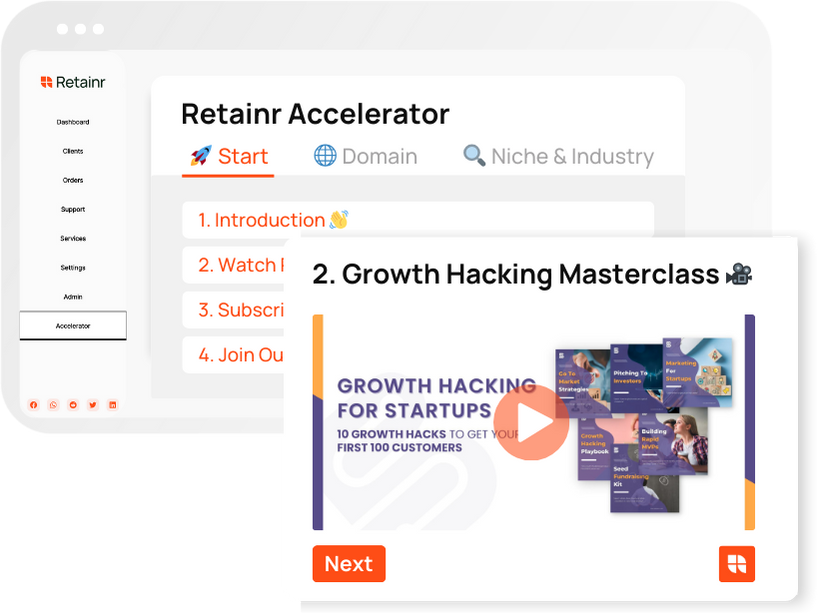
SOPs, Cheatsheets & Blueprints
Leverage 50+ SOPs (valued over $10K) offering practical guides, scripts, tools, hacks, templates, and cheat sheets to fast-track your startup's growth.
Connect with fellow entrepreneurs, share experiences, and get expert insights within our exclusive Facebook community.
.jpg)
Join a thriving community of growth hackers. Network, collaborate, and learn from like-minded entrepreneurs on a lifelong journey to success.
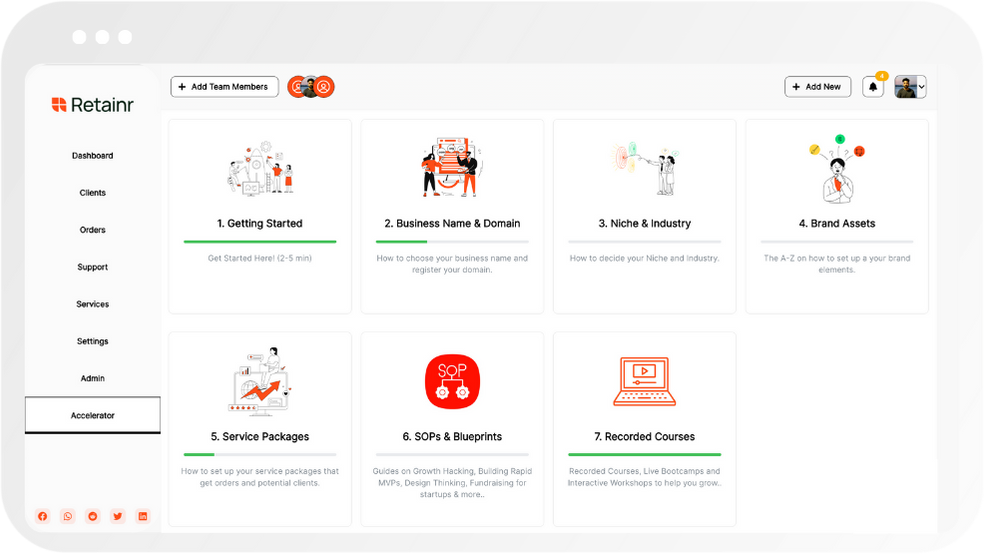
Gain expertise with recorded Courses, Live Bootcamps and interactive Workshops on topics like growth hacking, copywriting, no-code funnel building, performance marketing and more, taught by seasoned coaches & industry experts.

.jpg)

.jpeg)


